Last week, over 500GB of leaked confidential files—including source code, system logs, and internal communication records—exposed the inner workings of the so-called Great Firewall censorship system, revealing secretive projects from core contractor Jizhi Information Technology Co., Ltd., also known as Geedge Networks (led by Chief Scientist Fang Binxing, the father of the GFW, and Chief Technology Officer Zheng Chao) and the MESA Lab at the Chinese Academy of Sciences. This batch of files for the first time fully reveals the technical architecture and operational mechanisms of China's internet censorship system.
Domestically, Geedge Networks has established provincial censorship systems independent of the national Great Firewall in multiple provinces including Xinjiang, Jiangsu, and Fujian, which feature comprehensive network control functions including VPN identification and blocking, real-time online monitoring, DPI deep packet inspection, and detection of circumvention tools. The leaked files also once again confirm the provincial firewall independent operation model that was exposed in May of this year, marking a shift in China's internet censorship from centralization to tiered control.
Internationally, these censorship technologies are also being exported through the "Belt and Road" initiative. The leaked files show that Geedge has provided entire network censorship and surveillance systems to internet service providers in countries including Myanmar, Pakistan, Kazakhstan, and Ethiopia, as well as some unnamed countries, essentially replicating China's model of digital authoritarianism on a global scale. This technological proliferation threatens the internet freedom of civil society and bolsters the authoritarian rule of local governments.
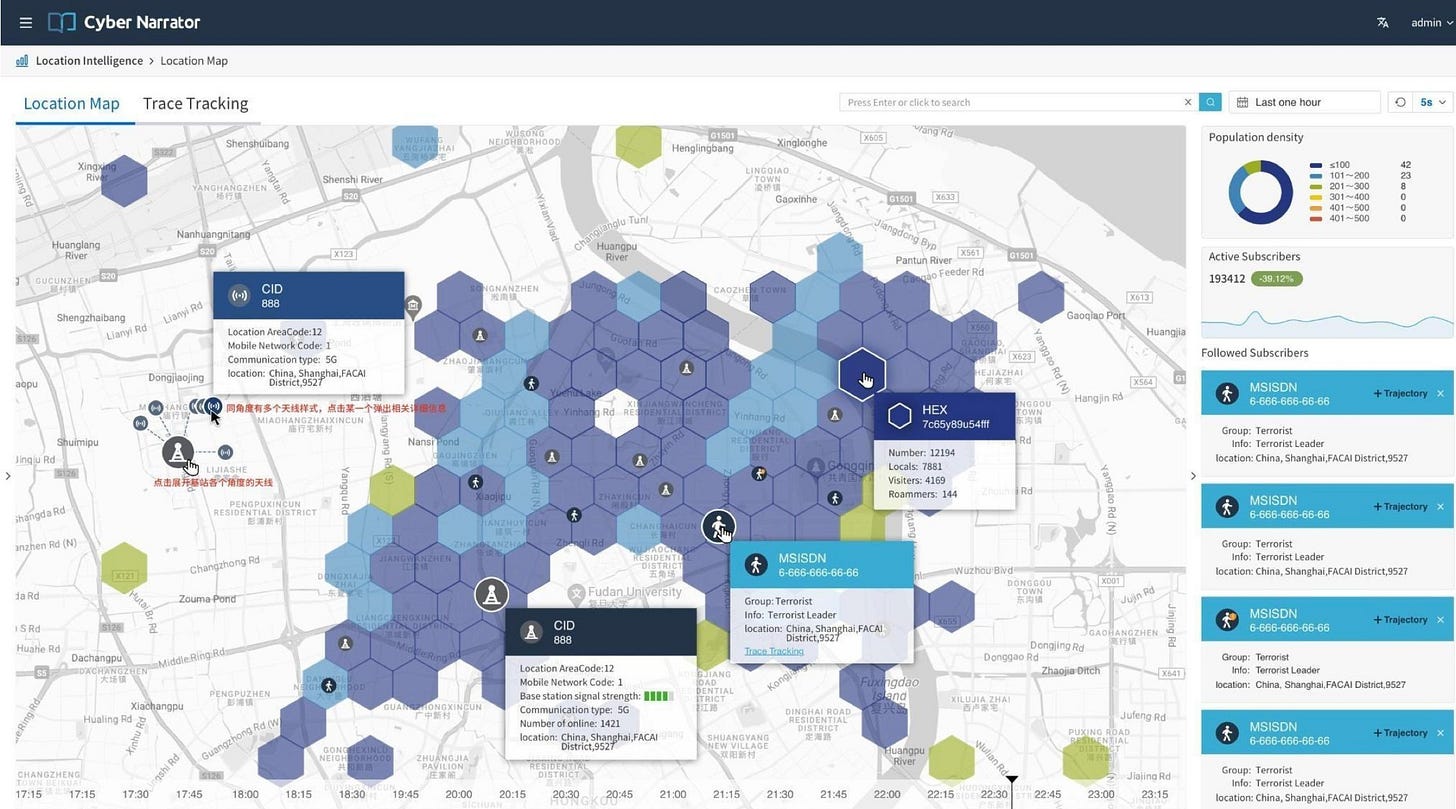
Perhaps most alarmingly, the leak has revealed increasingly sophisticated individual surveillance capabilities, including deep packet inspection, VPN/Tor/Psiphon detection, traffic shaping, malware injection, and dashboards that let governments track individuals and groups in real time. The system is developing geofencing functionality, which can automatically trigger alerts when specific individuals enter designated areas, and track users' historical location trajectories to reconstruct their activity patterns. The system specifically targets individuals who frequently change SIM cards, make international calls, or use circumvention tools and foreign social media, marking them to form a dynamic "high-risk user" database. Most threatening are the functional designs for group surveillance: it can display the real-time geographical distribution of monitored groups on a map and automatically detect abnormal personnel gatherings at specific locations, enabling operators to identify and predict the formation of large-scale protests and demonstrations in advance.
Further analysis of this leak is ongoing on multiple platforms.
This leak is one of the clearest windows yet into how digital authoritarianism is built, commercialized, and globalized. It confirms a strategic shift: censorship is no longer a centralized Chinese state function but a scalable product that is engineered, packaged, and exported under the Belt and Road Initiative (BRI). We are seeing the evolution from suppression of civil society to anticipatory repression. And Geedge's client base shows this model is spreading: more governments are gaining the ability to algorithmically predict potential dissent and neutralize it before it begins.
Governments, industry, and concerned citizens alike must understand the risks of allowing such a model to spread unchecked. Censorship as a service is being sold to governments who want it, stripping individuals of anonymity and facilitating predictive policing. Is this the digital future we are willing to accept?